The attack itself came from over 70,000 sources. It was composed of multiple Asia-Pacific countries such as Malaysia, Vietnam, Taiwan, Japan, China, and the United States.
Microsoft Azure Fends off huge DDoS Attack
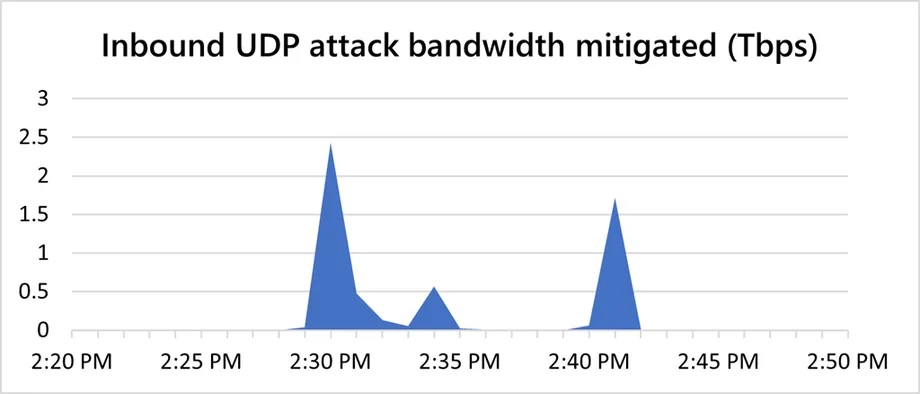
The attack vector was a User Datagram Protocol (UDP) reflection attack. The attack lasted over 10 minutes with very short-lived bursts. Each of these bursts ramped up in seconds to terabit volumes. In total, Microsoft saw three main peaks, the first at 2.4 Tbps, the second at 0.55 Tbps, and the third at 1.7 Tbps.
In a UDP reflection attack, the attacker exploits the fact that UDP is a stateless protocol. That means the attackers can create a valid UDP request packet listing the attack target’s IP address as the UDP source IP address. It looks as if the attack is being reflected back and forth within the local network, hence the name. This relies on the UDP request packet’s source Internet Protocol (IP) being spoofed. The UDP packet contains the spoofed source IP and is sent by the attacker to a middleman server. The server is tricked into sending its UDP response packets to the targeted victim IP rather than back to the attacker. The middleman machine helps strengthen the attack by generating network traffic that is several times larger than the request packet, thus amplifying the attack traffic. explains Amir Dahan, a senior program manager for Microsoft’s Azure networking team. Some DDoS protection is provided for all of Azure’s users. For better, more comprehensive protection, Microsoft recommends you subscribe to Azure DDoS Protection Standard. Besides blocking DDoS attacks, it also offers cost protection. This provides data transfer and application scale-out service credit for resource costs incurred because of documented DDoS attacks. Source: ZDnet